While this document is falsified and does not reflect any actual requirements for EU members or candidate countries, the last page provides a fake email address of a genuine EU Commission expert and a feedback form (both hosted on the same malicious domain europa[.]study):
 Figure 3 – Means to provide feedback (and therefore engage with the threat actors) provided in the disinformation document.
Figure 3 – Means to provide feedback (and therefore engage with the threat actors) provided in the disinformation document.
Another fraudulent document, designed to appear as if it was from the European Public Prosecutor’s Office (EPPO), targets Moldovan officials, specifically those in the judicial system:
 Figure 4 – Disinformation document claiming to be from the EPPO.
Figure 4 – Disinformation document claiming to be from the EPPO.
The document requests personal details and information about the commercial activities of close family members under the guise of adhering to the EU anti-corruption regulations. The data is supposed to be submitted via the form on the attacker-controlled domain impersonating EPPO, europa-eppo[.]eu. The document is not located on the actual EPPO document repository, does not follow the EPPO document template, and contains grammatical mistakes (such as “august” written in lowercase), indicating an obvious fake.
Victim data collection
All the fake forms have very similar code and a similar look.
![Figure 5 - Example of the first pages of the form on malicious
europa-eppo[.]eu site.](https://love-europe.com/wp-content/uploads/2024/10/1728484806_488_Operation-MiddleFloor-Disinformation-campaign-targets-Moldova-ahead-of-presidential-elections.png) Figure 5 – Example of the first pages of the form on malicious europa-eppo[.]eu site.
Figure 5 – Example of the first pages of the form on malicious europa-eppo[.]eu site.
The HTML of these forms loads an additional script, index.js: {
window.location.href=”https://www.eppo.europa.eu/en”
}, 1500);
]]>
The script logger.js is always the same: sha256: 4df435afa20401e3af2d17bf8dd67a9d8553520e29cc05905fc9458b8e81ce8f) –
it collects the user-agent, IP address data, and the current URL visited and posts the collected data to logger.php:
const getLogs = async () => {
const ipData = await fetch(“https://ipapi.co/json”)
.then((res) => res.json())
.then((data) => data);
const userAgent = window.navigator.userAgent;
const logs = {
page: window.location.href,
…ipData,
userAgent,
};
sendLogs(logs); };
const sendLogs = async (logs) => {
const data = new FormData();
for (param in logs) {
data.append(param, logs[param]); }
await fetch(“logger.php”, {
method: “POST”,
body: data, });
};
getLogs();
The response to this request contains yet another JSON message indicating successful interaction, this time with another Telegram Bot:
[omitted]
“is_bot”:true,”first_name”:”TESSET_BOT”,”username”:”TESSETTES_BOT”},”chat”:{“id”:-4586992285,”title”:”TES”,”type”:”group”,”all_members_are_administrators”:true}
[omitted]
It is evident that the threat actors have distinct notifications (and distinct Telegram bots) for victims who submitted the form and for any curious users (or researchers) who visit other pages.
Fake Migration policy changes
In early September, several organizations and institutions in the Republic of Moldova, including those from the education sector, received an email with an alleged “resolution” from the Ministry of Labor and Social Protection, with information about “changes in the migration policy.”
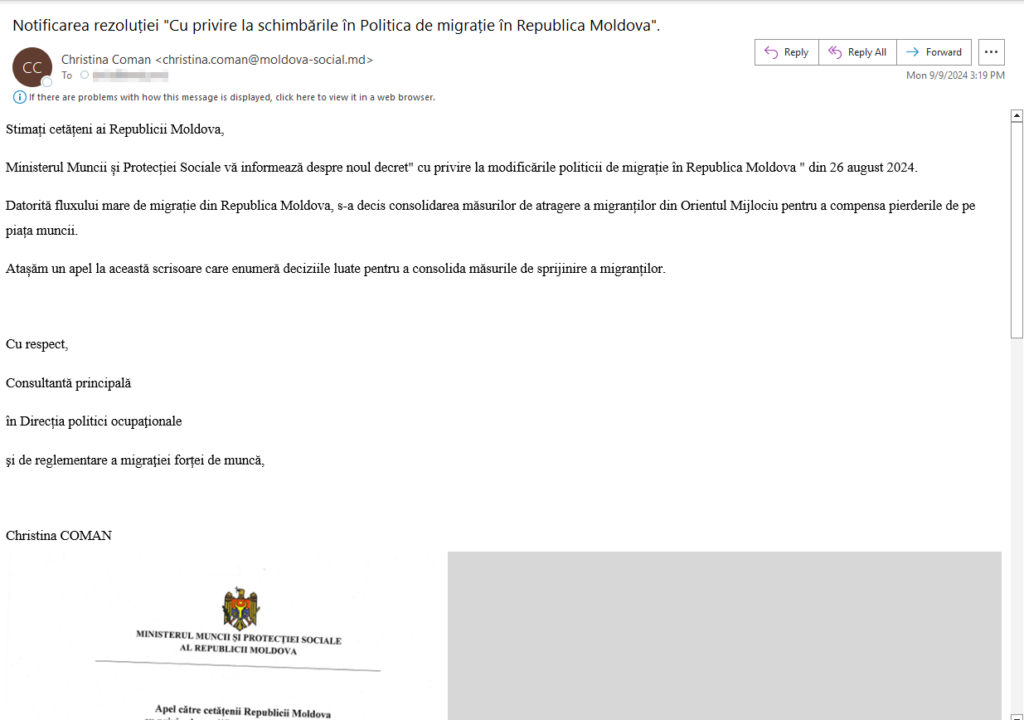 Figure 7 – An email with pictures of the fake resolution attached on the bottom. The email was sent from a fake Ministry of Labor and Social Protection address.
Figure 7 – An email with pictures of the fake resolution attached on the bottom. The email was sent from a fake Ministry of Labor and Social Protection address.
Translation of the email:
Dear citizens of the Republic of Moldova,
The Ministry of Labor and Social Protection informs you about the new decree “on changes to the migration policy in the Republic of Moldova” of August 26, 2024.
Due to the large flow of migration from the Republic of Moldova, it was decided to strengthen the measures to attract migrants from the Middle East to compensate for the losses on the labor market.
We are attaching an appeal to this letter outlining the decisions taken to strengthen measures to support migrants.
Sincerely,
Principal Consultant
in the Department for Employment and Labour Migration Regulation Policies
Christina COMAN
The attached fake document contains content about “strengthening measures to attract migrants from the Middle East to compensate for the losses on the labor market due to the large migration flow from Moldova.” Among other claims, it states that the percentage of migrants in every organization must be at least 30%, that new mosques will be built in every region of the country, and that a simplified process for obtaining citizenship will be implemented for migrants employed by Moldovan companies. Moldovan officials confirmed that the document is fake.
 Figure 8 – Fake document talking about radical migration policy changes.
Figure 8 – Fake document talking about radical migration policy changes.
Fake increase in gas prices and supply interruptions
Another troubling issue being exploited by the threat actors is the topic of gas prices for the upcoming winter. In mid-September, an email claiming to be from the Ministry of Energy stated that gas prices would increase and that planned interruptions to the natural gas supply would occur during the winter:
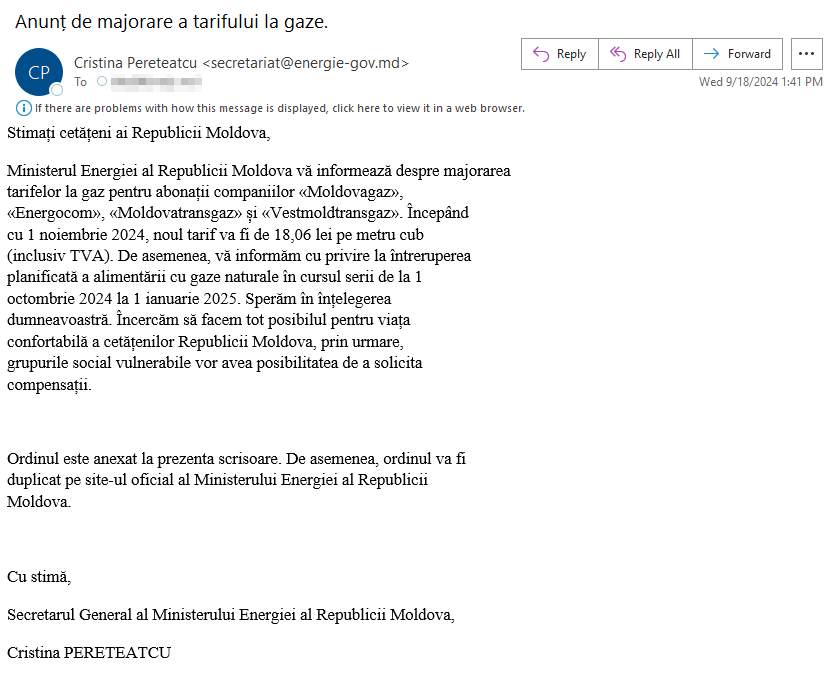 Figure 9 – Disinformation email about gas price increase.
Figure 9 – Disinformation email about gas price increase.
Translation:
Dear citizens of the Republic of Moldova,
The Ministry of Energy of the Republic of Moldova informs you about the increase gas tariffs for subscribers of “Moldovagaz” companies, “Energocom”, “Moldovatransgaz” and “Vestmoldtransgaz”. Beginning as of November 1, 2024, the new rate will be 18.06 lei per cubic meter (including VAT). We also inform you of the interruption planned supply of natural gas during the evening from 1 October 2024 to January 1, 2025. We hope for your understanding your. We try to do our best for life comfortable of the citizens of the Republic of Moldova, therefore, socially vulnerable groups will have the opportunity to apply compensations.
The order is attached to this letter. Also, the order will be duplicated on the official website of the Ministry of Energy of the Republic Moldova.
Sincerely,
Secretary General of the Ministry of Energy of the Republic of Moldova,
Cristina PERETEATCU
The Ministry of Energy already reported this message as disinformation. Despite attempts to make their emails appear legitimate, the threat actors confused the name of the General Secretary of the Ministry of Energy, Andrei Grițco, with that of the State Secretary within the Ministry of Energy, Cristina Pereteatcu.
Fake EU education values
Among the emails sent by the threat actors, some lacked attachments. One of these emails impersonated a member of the European Commission Cabinets using the spoofed domain europa-ec[.]eu and was sent to more than 80 recipients at one of the most prestigious universities in Europe:
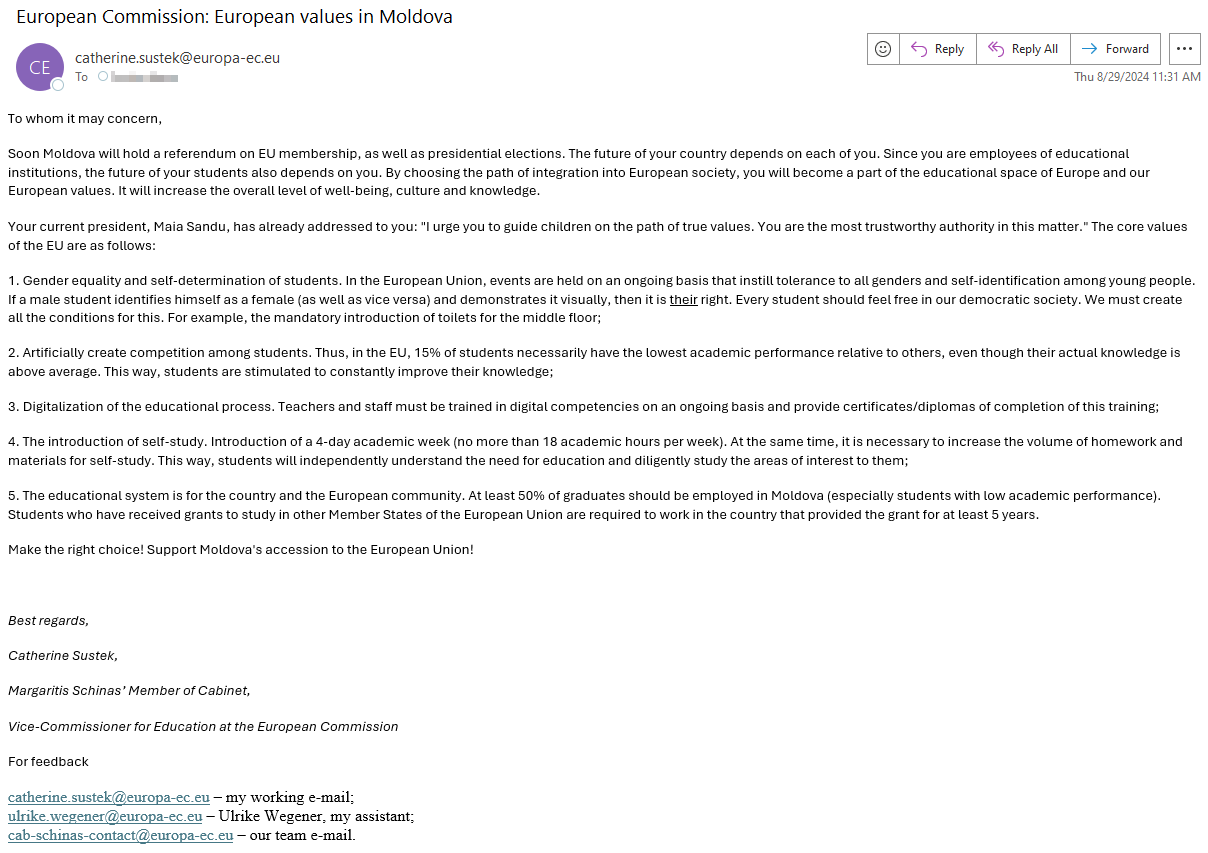 Figure 10 – A disinformation email regarding changes in the education system.
Figure 10 – A disinformation email regarding changes in the education system.
The email claims to promote a pro-European message, using the current president, Maia Sandu, as a source of inspiration, but spreads disinformation about European education values and standards. For example, deliberately lowering student grades to encourage academic growth is not accepted in European education policy or discourse. The email also features false restrictions on job opportunities for low-performing students and misleading requirements for working abroad within the EU. All these claims contradict the EU’s education policies, prioritizing equity, inclusion, and fairness.
The second wave of disinformation emails targeting employees of education institutions was sent on September 24 from a fake email domain impersonating the Moldovian Ministry of Education and Research. The emails contained PDF titled Privind aprobarea Programului ambasadorilor UE.pdf (“Regarding the approval of the EU Ambassador Program”). The PDF included a picture of the alleged official order from the Ministry, with content primarily focused on topics such as sex education and non-binary genders in context of educational institutions integration into the European Union.
Attribution
The email mentioned above about European education values was written in English yet contains some structural errors that suggest it was translated from another language. These include phrases such as “has already addressed to you” and “instill tolerance to all genders”, which are likely literal translations of those phrases from Russian.
The email’s first numbered point, which addresses gender equality, refers to “toilets for the middle floor”, a phrase that does not make sense in English. This is a literal translation from the Russian phrase «туалеты для среднего пола», meaning gender-neutral toilets.
Another argument supporting the Russian-speaking origins of Lying Pigeon is the metadata of both PDF documents which are purportedly from European institutions.
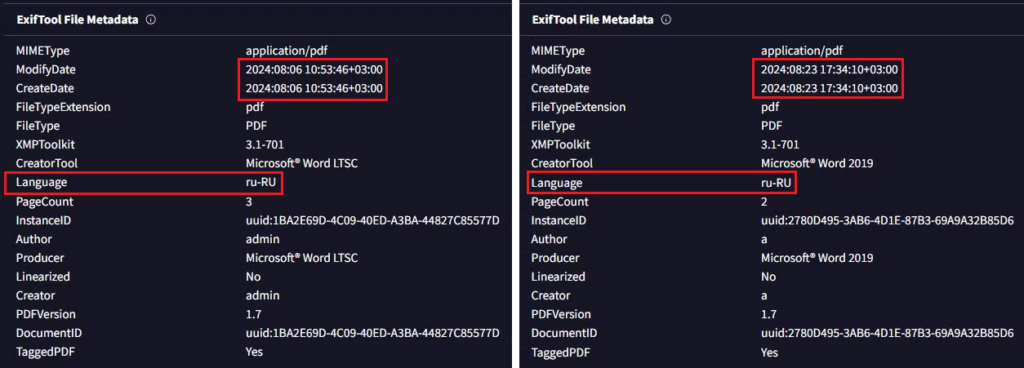 Figure 11 – Metadata of Letter_Directorate-General for Neighbourhood and Enlargement Negotiations.pdf (left) and Notification.pdf (right) PDFs impersonating the EU institutions.
Figure 11 – Metadata of Letter_Directorate-General for Neighbourhood and Enlargement Negotiations.pdf (left) and Notification.pdf (right) PDFs impersonating the EU institutions.
Both list ru-RU for Language metadata, meaning that the document was created using the Russian language local or regional setting. The document metadata lists UTC+3 for the time zone. A segment of the Moldavan population speaks Russian, and in August, the Moldavan time zone corresponds to UTC+3 due to Daylight Saving time; in addition, parts of Russia and Belarus, and some other countries in Eastern Europe, the Middle East, and Africa are located in the UTC+3 time zone.
Lying Pigeon infrastructure and past activity
Over the course of Operation MiddleFloor, the threat actors used a few domain name registrars to register the domains that spoof European and Moldovan entities:
Zone Media OÜ [Zone.EU] impersonates European Union entities, such as europa-eppo[.]eu.
NameCheap and Realtime Register B.V. for more generic domains such as gov-md[.]com.
Starting in September, the threat actors registered domains in .MD zone to impersonate Moldovan entities, such as energie-gov[.]md, for greater legitimacy.
All the domains and IP addresses used in this campaign are interconnected, enabling us to attribute these seemingly different techniques and messages to the same operation.
 Figure 12 – Maltego graph of the MiddleFloor infrastructure.
Figure 12 – Maltego graph of the MiddleFloor infrastructure.
All the servers used in this campaign can be classified into two categories:
Shared VPS on AS 200313 (IT WEB LTD) – For domain resolutions and hosting the forms. This hosting provider is often used by multiple threat actors to conduct malicious activities.
Dedicated mail servers – Hosted mostly on BlueVPS, the actors started to use OVH servers only since September 23. In the first half of the campaign, the threat actors used the email server mail.mailogon[.]online for a few different domains.
The threat actors use Mailcow, an open-source mail server suite, to host their own servers for anonymity and greater flexibility and to manage and scale their operations.
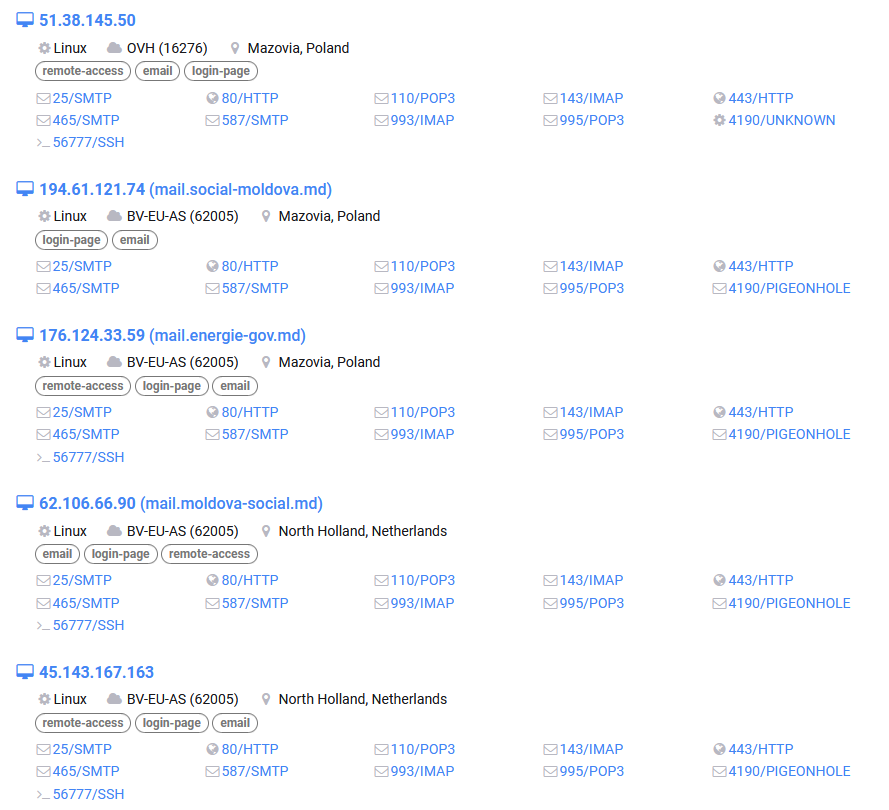 Figure 13 – Screenshot from censys.io showing the email servers currently used by the threat actors.
Figure 13 – Screenshot from censys.io showing the email servers currently used by the threat actors.
Connection to earlier activities
On August 6, one of the early domains related to Operation MiddleFloor, europa[.]study, and its Sogo subdomain was temporarily resolved to 185.255.132[.]69 hosted on AS 204997 (First Server Limited).
![Figure 14 - DNS resolutions of europa[.]study.](https://love-europe.com/wp-content/uploads/2024/10/1728484807_509_Operation-MiddleFloor-Disinformation-campaign-targets-Moldova-ahead-of-presidential-elections.png) Figure 14 – DNS resolutions of europa[.]study.
Figure 14 – DNS resolutions of europa[.]study.
In the period of November 2023 – March 2024, this IP also hosted another cluster of domains:
otllook[.]com, sapsap[.]site (also autoconfig.sapsap[.]site and autodiscover.sapsap[.]site), te-storg[.]com (also autoconfig.te-storg[.]com and autodiscover.te-storg[.]com), mailorun[.]su (also mail.mailorun[.]su, autodiscover.mailorun[.]su and autoconfig.mailorun[.]su).
We determined that this cluster likely belongs to the same threat actors responsible for the MiddleFloor operation due to the following reasons:
Judging by the certificates, all these “old” domains belong to the same actor.
No other activity has been observed on this IP address since then.
The IP address 185.255.132[.]69 hosted an email server with a similar Mailcow and Let’s Encrypt certificate setup.
One of these domains, mailorun[.]su, mimics Mailgun; the MiddleFloor campaign also used the domain mailgon[.]online.
Most of these domains – otllook[.]com, mailorun[.]su, and te-storg[.]com – are registered with the same email address: gotohends@inbox[.]eu. In addition, over time, a few more domains were registered with this same email address:
vilnius-summit[.]lt
litexpo-portal[.]lt
viilnius[.]lt
nask-pl[.]com
sso-log[.]com
This set of domains creates multiple additional pivot points, such as the IP address 45.133.148[.]35 and shared mail server, mail.mailos[.]ru.
Based on these domains and their pivots, we identified a few additional clusters of Lying Pigeon’s previous activity. We suspect that those domains that are resolved to specific IP address, have an SPF record an MX record pointing to the same IP, were likely meant to send spoofed emails.
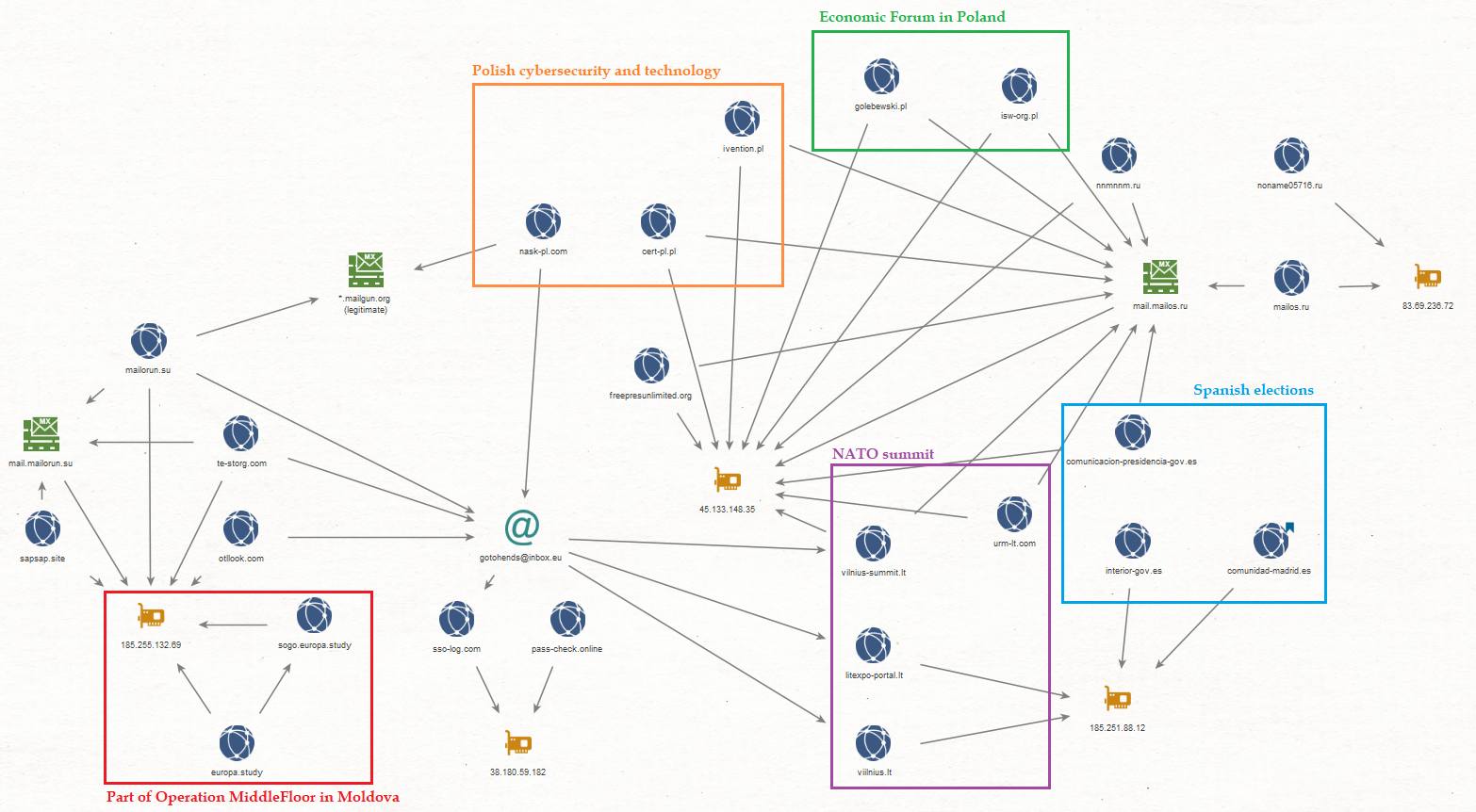 Figure 15 – Lying Pigeon infrastructure over the years and clusters of their activity and interests.
Figure 15 – Lying Pigeon infrastructure over the years and clusters of their activity and interests.
2023 NATO summit and Lithuanian entities
The 32nd formal meeting of the heads of state and governments of the thirty-one members of the North Atlantic Treaty Organization, their partner countries, and the European Union, was held in Vilnius, Lithuania, on July 11-12, 2023. This cluster of domains was observed within a short time frame around the event.
DomainEntity spoofedIP resolutionASNTime framevilnius-summit[.]ltNATO summit45.133.148[.]35AS 49505
(JSC Selectel)08.07.2023 – 12.07.2023urm-lt[.]comLithuanian Ministry of Foreign Affairs45.133.148[.]35AS 49505
(JSC Selectel)11.07.2023 – 08.04 2024viilnius[.]ltLithuanian capital185.251.88[.]12AS 35278
(Sprinthost.ru LLC)12.07.2023 – 13.07.2023litexpo-portal[.]ltLITEXPO, NATO summit venue185.251.88[.]12AS 35278
(Sprinthost.ru LLC)12.07.2023 – 13.07.2023
2023 General Elections in Spain
The Spanish general election to elect members of the Congress of Deputies and the Senate, which comprise the country’s legislative parliament was held on July 23, 2023. Pivoting on existing domains and IP addresses, this cluster of activity includes the following domains, all of whom existed around the election date:
DomainEntity spoofedIP resolutionASNTime framecomunicacion-presidencia-gov[.]esCommunication office of the Presidency45.133.148[.]35AS 49505
(JSC Selectel)22.07.2023-23.07.2023comunidad-madrid[.]esCommunity of Madrid185.251.88[.]12AS 35278
(Sprinthost.ru LLC)22.07.2023-23.07.2023interior-gov[.]esMinistry of the Interior (Spain)185.251.88[.]12AS 35278
(Sprinthost.ru LLC)23.07.2023
The last two domains were observed as part of a disinformation campaign discovered by QuoIntelligence. This campaign was targeting Russian-speaking communities in Spain the day before the elections with Telegram messages that linked to a fake website mimicking the website of the Community of Madrid. The fake website contained a warning from the Ministry of Interior about a planned series of attacks by the ETA, a Basque separatist organization. The message encouraged recipients to skip voting in the elections to avoid risking their lives. QuoIntelligence researchers also noted that the campaign used fewer delivery methods (e.g., no email-based vectors or massive social media campaigns) to spread the message. We suspect that the first domain in this cluster, comunicacion-presidencia-gov[.]es, which contains MX records pointing to the mail server mail.mailos[.]ru at the same time, might have been used for email-based attacks, but as of now do not have any firm evidence.
 Figure 16 – Web archive copy of the fake terrorist attack warning.
Figure 16 – Web archive copy of the fake terrorist attack warning.
XXXII Economic Forum in Karpacz, Poland
The Economic Forum took place from September 5-7, 2023, in Karpacz. It attracted over 5,400 participants, including politicians, business leaders, and cultural figures from across Europe and other continents. The Forum featured a wide range of discussions, debates, and special sessions on crucial topics like the economy, security, and the future of Europe.
DomainEntity spoofedIP resolutionASNTime frameisw-org[.]plFundacja Instytut Studiów Wschodnich (Foundation Institute of Eastern Studies) which organized Economic Forum45.133.148[.]35AS 49505
(JSC Selectel)02.09.2023- 9.07.2023golebewski[.]plThe Gołębiewski Hotel in Karpacz where the Forum took place at45.133.148[.]35AS 49505
(JSC Selectel)02.09.2023 – 08.09.2023
Poland cybersecurity and technology cluster — Connection with APT-UNK2
DomainEntity spoofedIP resolutionTime frameTime framecert-pl[.]plCERT Polska45.133.148[.]35AS 49505
(JSC Selectel)23.08.2023 – 06.09.2023ivention[.]plEvention.pl, hosted the KSC Forum in Poland in August 2023.45.133.148[.]35AS 49505
(JSC Selectel)04.08.2023 – 08.09.2023nask-pl[.]comNASK – National Research Institute under the supervision of the Polish Ministry of Digital Affairs.194.58.112[.]174 (REG.RU default shared IP), MX pointing to legitimate mailgun.org serversAS 197695
(Domain names registrar REG.RU )28.09.2023 – 31.03.2024
The CERT Polska report:
CERT Polska reported that the threat actor they track as APT-UNK2 carried out a campaign involving the impersonation of NASK (a Polish research and development organization, data networks operator, and internet domain name registry operator for the .pl country-level top-level domain). The campaign used the domain nask-pl[.]com to distribute emails, which contained an attachment that included a PDF (md5: cff5b518a247756febc43386ad1ecc88) with instructions and a Dropbox link for installing malicious Network_CPP_Shield.msi (md5: 609c677a134efac42bfefe6d58451caf). Victims’ machines were infected with the Lumma Infostealer.
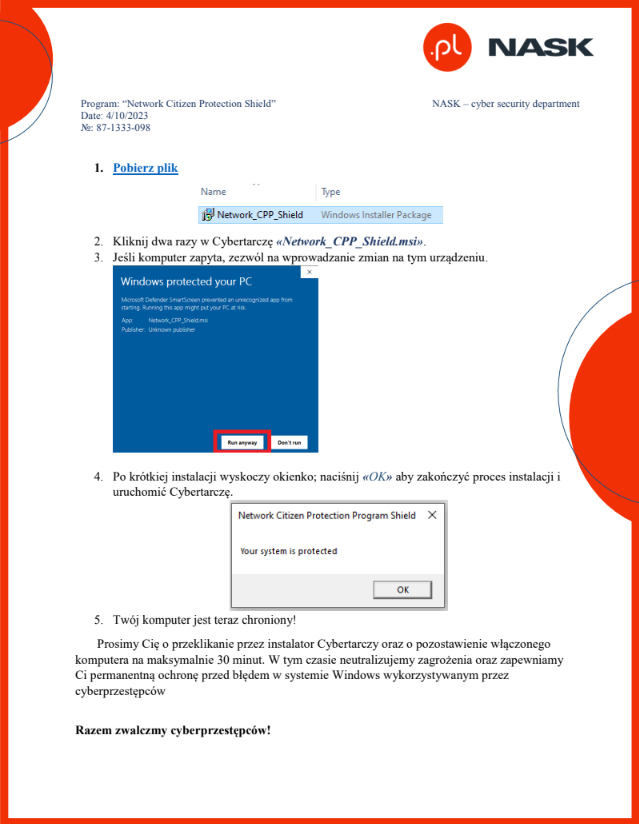 Figure 17 – Fake “CPP Shield installation instructions” from the NASK.
Figure 17 – Fake “CPP Shield installation instructions” from the NASK.
Other domains
Other domains that didn’t fit the clusters described above:
DomainCommentIP resolutionASNTime framefreepresunlimited[.]orgSpoofs Free Press Unlimited, an NGO focused on international press freedom45.133.148[.]35AS 49505
(JSC Selectel)04.08.2023 – 31.03.2024nnmnnm[.]ruRefers to Noname057(16), pro-Russian hacker group also known as 05716nnm or Nnm0571645.133.148[.]35AS 49505
(JSC Selectel)24.01.2023 – 15.09.2024noname05716[.]ruRefers to Noname057(16), pro-Russian hacker group83.69.236[.]72AS 12616
(Citytelecom LLC)23.01.2023 – 21.01.2024sso-log[.]comRefers to login activity38.180.59[.]182AS 9009
(M247 Europe SRL)22.03.2024 – 10.02.2024pass-check[.]onlineRefers to login activity38.180.59[.]182AS 9009
(M247 Europe SRL)06.05.2024 – 01.09.2024
Some interesting patterns we observed:
Domains sso-log[.]com and pass-check[.]online (pivoted on the same IP addresses during the same timeframe): Judging by their names, we assume these are for use in web-based credential phishing attacks.
Domain nnmnnm[.]ru which also has the same email server mailos[.]ru, and noname05716[.]ru which was resolved to the same IP address as mailos[.]ru in the same timeframe. Both refer to the infamous Noname057(16) pro-Russian hacktivist group, which is known for its DDoS attacks against NATO countries. As the group never mentioned their sites in their public communications, it’s unclear what relationship, if any, exists between Lying Pigeon and Noname057(16).
Conclusion
The disinformation campaign led by Lying Pigeon represents a significant and ongoing threat to the political stability of the Republic of Moldova, particularly as the campaign seeks to influence the outcomes of both national elections and the EU membership referendum. Our investigation also connected Lying Pigeon to previous election interference activities in Spain in 2023, highlighting their persistent involvement in undermining European democratic processes. Additionally, this group has been active around major European events, such as the NATO summit and the European Economic Forum, likely using these high-profile occasions to further their disinformation efforts.
Beyond their influence operations, Lying Pigeon likely uses their campaigns to distribute infostealer malware and collect sensitive information for future targeted attacks. This dual approach of combining disinformation with information harvesting underscores the sophisticated and multifaceted nature of Lying Pigeon’s operations, making them a critical threat actor to monitor in the ongoing struggle to protect democratic integrity and ensure cybersecurity in Europe.
Indicators of Compromise
Middle Floor Cluster
europa[.]study
europa[.]social
europa-ec[.]eu
europa-eppo[.]eu
gov-md[.]com
moldova-social[.]md
social-moldova[.]md
moldova-energie[.]md
energie-gov[.]md
socialisti[.]md
socialistii[.]com
mec-gov[.]md
md-mec[.]com
moldova-mediu[.]md
eupm-moldova[.]md
mcgov[.]md
mc-md[.]com
mailgon[.]online
fb9105dc73a52d36a612157536322a7d3630c813f6acf1b997b370cfd768118c
9a06192d3d922b1e4c404d2c9bac43d3315040635c472257c7a28f51b078ccfe
0e295605cfb9d922ff94d38cad5743da9e3d7d8feddee7b42ca3e2314133a0f0
5c34498dfab981a4d9fb2b898d4e965ae7378e066bbf01ae29bc61adf1a66b2d
Mail servers
62.106.66[.]90
194.61.121[.]74
176.124.33[.]59
185.255.132[.]69
45.143.167[.]163
51.38.145[.]50
194.61.121[.]131
Lithuanian Cluster
vilnius-summit[.]lt
urm-lt[.]com
viilnius[.]lt
litexpo-portal[.]lt
Spanish Cluster
comunicacion-presidencia-gov[.]es
comunidad-madrid[.]es
interior-gov[.]es
Polish clusters
cert-pl[.]pl
ivention[.]pl
nask-pl[.]com
isw-org[.]pl
golebewski[.]pl
c8c3bcdb856b9acffa853124ed13a0cc96641691233004cbe9bf8e018edb8f1b
d1b285fbe249349ae167052d81b4ab5d7e78c14e1ae617ef0985cc101a119d82
Uncategorized domains
freepresunlimited[.]org
nnmnnm[.]ru
noname05716[.]ru
sso-log[.]com
pass-check[.]online
mailos[.]ru
mailorun[.]su
otllook[.]com
sapsap[.]site
te-storg[.]com
Source link : https://research.checkpoint.com/2024/disinformation-campaign-moldova/
Author :
Publish date : 2024-10-09 13:24:47
Copyright for syndicated content belongs to the linked Source.


